How to use it to your advantage and improve your department’s ability to respond to IT-outage and cyber threats.
I’m sure lots of you out there have been dealing with the impact of the recent CrowdStrike outage. Us too! So much so that it’s taken a couple days just to get this out because we’ve been dealing with the medical device and organizational impacts.
This entire experience has been an excellent example of multiple aspects of cybersecurity and basic IT disaster preparedness. Though everything I have seen indicates this was NOT a cybersecurity incident and was the result of some faulty code, and perhaps a lapse in quality control, it served as an excellent demonstration of negative impacts to medical technology and patient care.
Now is a good opportunity to put your incident response plan into action as well as add some additional workflows to it for non-cybersecurity related outages and test it’s effectiveness in a, relatively, lower impact event. It galvanized frontline staff to the importance of disaster recovery planning and that our medical technology is not immune to IT-related outages – that could potentially be the result of a cyber attack.
Some of the observed impacts from this particular outage – in no particular order:
- Lack of back-ups to get systems operational in a short period of time
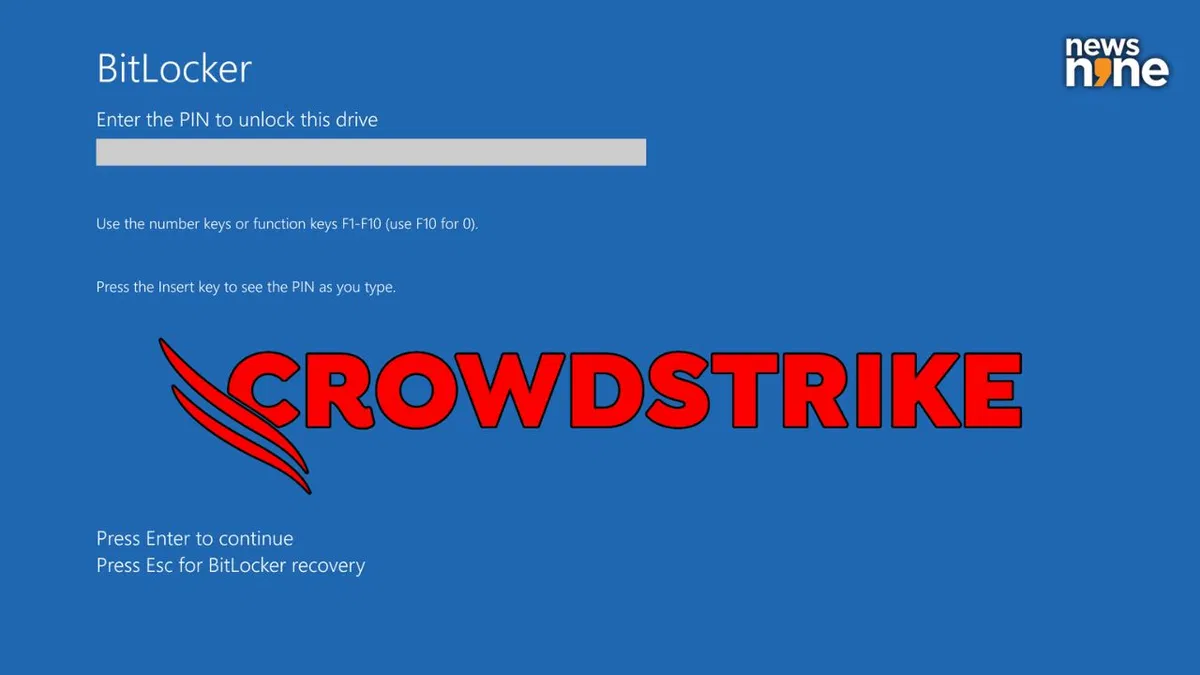
- Equipment with OEM BitLocker encryption but you don’t have the encryption keys – this means the only recovery is a total system reload when all that was needed was to delete the corrupted file and reboot.
- This was a significant impact – what could have been done in 10 minutes quickly meant equipment was out for 60+ minutes. Multiplied by 10’s of systems and the outage quickly escalated.
- incomplete or non-existent installation media from the OEM.
- inconsistent configuration back ups or very dated back ups made them of limited use.
- Focus on getting systems operational means some configurations were neglected (CrowdStrike (A/V) installs, WSUS server configs, etc.)
- This means that all systems will have to be “touched” again and this increases the time/workload of the outage on front-line staff
The Opportunity
Once the bulk of the work is complete and systems are operational and available for clinical staff and patients it would be a good time to take stock of the outage and your ability to respond. Look for gaps in your response and what took the most time to remedy. How was the communication at all levels? Did information flow easily and get disseminated to the people who needed it in a timely manner? Were some vendors better prepared than others? – You get the point 🙂
We have gathered some resources here.
We would love to hear your experiences and successes during what has been a trying time for HTM/Biomed. Feel free to reach out or leave a comment below.

Leave a Reply
You must be logged in to post a comment.